Malware types, symptoms, protection, prevention and removal
Malware is software designed to damage or disrupt a computer system, server, or network, steal information, and more. Learn more about malware.
Malware (short for malicious software) is software designed to damage or disrupt a computer system, server, or network, steal information, hijack your files for ransom, gain unauthorized access to information or systems, or destroy data.
What are the types of malware?
There are different types of malware, such as computer viruses, ransomware, spyware, rootkits, worms, trojans, keyloggers, adware, botnets, rogue security software, and crypto-mining malware.
A Computer virus is capable of copying itself and spreading to other computers. Computer viruses can perform harmful activities such as corrupting the system or destroying data.
Ransomware prevents or limits users from accessing their systems or data. Ransomware forces its victims to pay the ransom through online payment methods to grant access to their system or get their data back.
Spyware secretly and quietly monitors your activities and gathers your information through your Internet connection without you knowing about it.
Adware shows unwanted advertisements on your computer and generates revenue for its creator. These advertisements are often in the form of annoying pop-up windows.
A Trojan disguises itself as a normal file or program to trick users into downloading and installing malware.
A Keylogger runs quietly in the background and records every keystroke you make (everything you type on your keyboard). These keystrokes can include usernames, passwords, credit card numbers, and other personal data. The keylogger will share this information with its creator.
A Rootkit is a collection of tools (programs) designed to remotely access or control a computer or network without being detected. They're difficult to detect because they start running before your computer's operating system has completely started.
A Worm is capable of copying itself and spreading to other computers. Worms use networks to spread themselves and cause harm by hogging bandwidth (this makes your internet slow) or possibly deleting files or sending documents via email. Worms can also install backdoors on computers. The difference between a worm and a computer virus is that worms spread across networks, and computer viruses attach themselves to various programs and executable codes.
A Botnet is a network of malware-infected computers that are controlled by the creator of the botnet (cybercriminal). Each computer functions as a bot because it's infected with a specific type of malware. A botnet can be used to send spam emails, transmit malware, perform DDoS attacks and perform other malicious tasks.
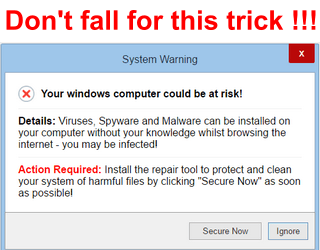
Rogue security software (Rogueware) often pretends to be security software such as antivirus and antimalware software, but can also pretend to be other software such as system cleaners. This type of malware is simply misleading, fake software that asks users to pay money for removing fake problems and threats.
Crypto-mining malware uses system resources to mine for cryptocurrency without the owner's permission.
What are the symptoms of malware?
- Your computer, web browser, server, or internet are much slower than usual
- Your computer or web browser often freezes or crashes
- There are files modified or deleted without your doing
- The hard drive continues to have excessive activity — even when you don't use it
- Sudden increase of disk space on your hard drive
- Annoying unwanted pop-up windows or ads appear
- Unusual high network activity when you're not using your web browser
- Your web browser's homepage has changed without your doing
- Your web browser has a new toolbar
- When you're trying to open a website and your web browser redirects you to another website
- Programs start without your doing
- Your antivirus software is disabled
- Your contacts receive messages or emails from you that you didn't send
- You're blocked from accessing your system or files and are forced to pay money (ransom) to regain access again
- Your computer automatically plays music
- There are new unknown icons on your desktop
- Your computer restarts by itself
How to protect against malware
The BEST malware protection is YOU.
Look:
You can have the best malware protection on your computer, but even the best anti-malware (antivirus) software can fail to detect new malware.
Malware threats have grown significantly in the past decade. And these threats grow so fast that antivirus programs take too long to catch up with malware (even the best programs).
Therefore, the best protection is yourself.
Educate yourself about malware and other cyber threats. Get some basic understanding, and you'll be much safer online and offline.
There's no better protection against malware than yourself, so pay attention to everything you do, online and offline.
Always use antivirus software on your computer – even when antivirus programs can't protect you 100% against all malware.
But:
It's better to have some protection than no protection at all.
And:
Antivirus software can protect you against most known malware.
You should always install and use only one antivirus program on your computer.
Using multiple antivirus programs on a PC is a bad idea! Because:
- They might attack each other because one of them might think that the other one is malware. After all, it's monitoring your system (like spyware or other malware), and then it will attempt to block and remove it.
- They will fight over malware because if one detects malware and moves it in quarantine, the other might also find the same malware (even when the other program already has it in quarantine). And it will also try to remove the malware and place it in quarantine. Then you will keep getting the same notifications about this malware over and over again.
- They will make your system slow because antivirus programs use a lot of your system memory to perform system scans and other related tasks. So your system will become slower when using two antivirus programs.
There are so many free and paid antivirus programs out there that it's sometimes hard to choose one.
The free antivirus I recommend is Microsoft Defender (formerly known as Windows Defender).
Microsoft Defender is already built-into Windows 10 and 11.
Microsoft Defender and common sense offer enough protection against most types of malware.
Another option is Bitdefender Antivirus Free.
If you need more functions (e.g., multi-layer ransomware protection) and settings, then you can try a paid antivirus program.
Many antivirus companies offer a free 30-day trial.
The paid antivirus programs I recommend are Bitdefender Antivirus or ESET Antivirus.
You can also use second opinion malware scanners to scan your computer for malware. You can use malware scanners to scan your computer for malware periodically (e.g., once a week) or when you think your computer is infected. You can use second opinion malware scanners alongside your current antivirus software without a problem.
The malware scanners I recommend are Kaspersky Virus Removal Tool, ESET Online Scanner, and Emsisoft Emergency Kit.
Other options are Malwarebytes and Norton Power Eraser.
If you're using GNU/Linux as an operating system and your day-to-day security practices are good, and your operating system is up-to-date, you don't need an antivirus because Linux malware is still rare at the moment.
How to prevent malware
- Keep your operating system, web browser, and other software always up-to-date.
- Use a firewall (Windows firewall is enough).
- Always take security warnings from your antivirus program seriously. Never ignore security warnings!
- Don't download and use pirated software.
- Never click on OK, Yes or Run when a pop-up window appears and asks you to download and install unknown software.
- Never click to fast on Next, Install, OK, etc. when installing software, because you might install extra unwanted third-party software (like toolbars). If you see extra offers, then uncheck all their checkboxes.
- Always download software from the official link or a trusted website.
- Don't click on links in emails from unknown senders.
- Don't download and open email attachments – unless you can verify the source.
- Check free software before downloading and installing it on your computer. Just Google the software first and look for reviews or forums.
- Use a secure and safe web browser like Google Chrome, Mozilla Firefox, Microsoft Edge, or Brave and keep it updated.
- Don't click on links you don't trust, but first, check the link. When you go with your mouse cursor on the link, then you can see at the bottom left corner of your browser window the REAL location the link is pointing to. You can also check the link using VirusTotal.com.
- Never download codecs or players to watch videos online. If you can't play the video online in your secure web browser then there's something wrong with the video or website.
- When you insert a USB flash drive or external hard drive from someone else into your PC, then scan it first with your antivirus program before opening or copying anything.
- If you want to take risks, then at least install VirtualBox on your PC, then install an operating system, like GNU/Linux (Linux Mint or Ubuntu) as a virtual machine in VirtualBox and do your risky things in there. But remember that also this is NOT 100% safe.
- Don't use a Windows administrator account for daily use, but use a standard account instead. If malware or a hacker gets access to your system, then the malware or hacker has the same rights to whatever account you're using. So if you use an administrator account and malware or a hacker takes control of your system, then the malware or hacker can do anything he, she or it wants and have full control of your system, but if you use a standard account then they can only do things that don't require administrator permission, so he or she can't change important system settings or install malware, and malware can't install itself unless you enter the administrator password.
- If you are curious about a file or link, then you can also analyze it on www.virustotal.com.
How to remove Malware for free
This tutorial will show you how to remove malware from your computer using free second opinion malware scanners.
You can use second opinion malware scanners alongside your current antivirus software without a problem.
Important tips!
- Create a system restore point. If something goes wrong, you can restore the mistake with a system restore point.
- Scan your computer with multiple malware scanners because some programs may detect malware that others might miss.
- Double-check the results of each scan and make sure that nothing important is selected for removal. Even malware scanners can make mistakes and sometimes see something harmless as a threat.
- If you have problems installing or opening malware scanners, start Windows in “Safe Mode with Networking” and try again.
Recommended solution
If your computer is infected with malware, and you want to be 100% sure that your system will be clean, then the best solution is to back up any data you might have and reinstall Windows or restore a system image backup that is 100% clean.
Why?
Well, if your antivirus (antimalware) software detected malware, then you will never know for sure if that is the only piece of malware that has infected your system.
Malware can nestle itself deep into your system and hide, and then it cannot be found by your security software.
Malware can also open doors to other malware.
And:
You may also end up with a damaged Windows operating system.
Considering time and effort, sometimes it is better to stop trying to clean your infected computer and just nuke it and reinstall Windows.
If you still want to try removing malware, follow the steps below.
With the following steps, I assume that you have access to your system or, at least, can boot into Safe Mode with Networking.
But, if you cannot access your system or boot into safe mode, you can use Kaspersky Rescue Disk.
Once you have the ISO file, you can install it on a USB flash drive with the help of a free tool called Rufus, and then you can boot from the USB drive and use the rescue disk.
Step 1: Find out if your files are affected by Ransomware
If you cannot open some files on your computer or see files with missing or weird file extensions (e.g., .cry, .crypto, .locked, .kraken), your system is probably infected by Ransomware.
If your system is infected by Ransomware, the first thing you should do is to check if your files can be decrypted.
But to do this, you first need to find out which Ransomware has infected your PC.
To find out which Ransomware has infected your PC, look at the ransom note, look at messages on the screen, or look at the encrypted files and the extension they have.
If you cannot find out which Ransomware infected your PC, you can visit ID Ransomware by MalwareHunterTeam and upload the ransom note or an encrypted file.
You can also visit a cybersecurity forum like BleepingComputer. On this forum, you can find a lot of malware analysts that you can talk to.
You can post something in the forums and upload one of your encrypted files.
They might be able to tell you whether or not you can decrypt your files.
You can visit NoMoreRansom.org or the free ransomware decryptors page on Kaspersky.com and check if they have a decryptor tool for the Ransomware that infected your PC.
Step 2: Make a backup of your files
Back up your files if they weren't affected by Ransomware.
You can use a free backup program like AOMEI Backupper Standard or copy your files to a USB flash drive or external hard drive.
Step 3: Use Rkill to terminate malicious processes
1. Download the Rkill setup file from BleepingComputer.com.
2. Double-click on iExplorer.exe to run Rkill.
3. Wait for Rkill to terminate malicious processes.
Step 4: Scan your computer with malware scanners
You can use second opinion malware scanners to scan your computer for malware, and hopefully, also remove malware.
You can use malware scanners alongside your current antivirus software without a problem.
The malware scanners I recommend are Kaspersky Virus Removal Tool, ESET Online Scanner, and Emsisoft Emergency Kit.
Other options are Malwarebytes and Norton Power Eraser.
These malware scanners work pretty much the same way. You download them, open them, and click a button to start a scan.
Make sure to double-check the scan results and uncheck everything harmless before you click to continue the removal process. Malware scanners might detect something as a threat when it isn't a threat.
Hopefully, you learned enough about malware to keep you, your data, and your computer safe.
Related:
Computer virus types, symptoms, protection and prevention
How to stay safe online (internet safety tips)
References:
https://en.wikipedia.org/wiki/Malware
https://www.webopedia.com/definitions/spyware/
https://en.wikipedia.org/wiki/Adware
https://www.techtarget.com/searchsecurity/definition/rootkit
https://www.webopedia.com/definitions/trojan-horse/
https://www.nortonlifelockpartner.com/security-center/computer-worms.html
https://usa.kaspersky.com/resource-center/threats/computer-viruses-vs-worms
https://www.trendmicro.com/vinfo/us/security/definition/Ransomware
https://www.webopedia.com/definitions/keylogger/
https://us.norton.com/internetsecurity-malware-what-is-a-botnet.html
https://www.webopedia.com/definitions/cryptomining-malware/
https://heimdalsecurity.com/blog/warning-signs-operating-system-infected-malware/
https://www.lastline.com/labsblog/antivirus-isnt-dead-it-just-cant-keep-up/
https://www.kaspersky.com/blog/multiple-antivirus-programs-bad-idea/2670/
https://help.ubuntu.com/stable/ubuntu-help/net-antivirus.html.en